
It doesn’t matter how much you spend on firewalls, anti-virus software or other proven IT security technologies if it can all be compromised by a single employee’s mistake or malice.
Indeed, that’s exactly what happened when the names, addresses, emails (and even Social Security Number-equivalents) of more than 100 Equifax employees were protected by nothing more than a weak username and password: “admin” (CNBC).
Firstly, small and medium-sized businesses (SMB) aren’t immune to cyber attacks; on the contrary, TechRepublic states, “negligent employees are the no. 1 cause of data breaches at small and medium-sized businesses across North America and the UK.”
Secondly, cyber attacks are incredibly costly for SMBs. According to a 2018 study by Cisco, 54% of the SMBs surveyed said that cyber attacks had cost each of them, on average, over $500,000 in “lost revenue, customers, opportunities, and out-of-pocket costs.”
Costs of this magnitude are catastrophic for most SMBs, yet it can only take one employee’s mistake or oversight to trigger those losses and cause lasting damage to your business.
System downtime following a severe breach
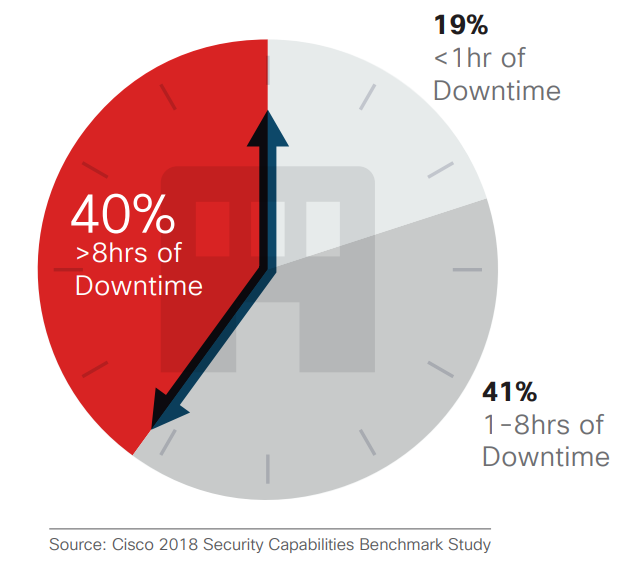
Source: Cisco
Cyber Security Breaches Caused by Employees
Employees manifest in two forms of cyber risks:
-
Human Error
Whether it is a lack of seriousness, training or both, poor employee decisions — such as using weak passwords, sharing passwords with friends and family, not taking care of their devices or others — are critical cyber security risks.
-
Insider Attacks
SMBs also face the risk of malicious insiders who are actively seeking and exploiting gaps in IT as a means to steal money and information and/or cause damage.
While the outcome in the very end is similar (such as a data breach), they occur as a result of different causes, each requiring its own cyber security solutions.
Learn More:
- How Your Employees are Your Biggest Cyber Security Risk
- What is Cyber Security Training and How Does It Improve IT Security?
Human Error Data Breach
Regarding the human error, the problem squarely rests on the training, awareness and sensibilities of your employees.
For example, your employees are a major risk-factor when they are unable to spot a potential phishing attack, such as mistaking a false login portal to their bank and logging into it.
Similarly, they might fall for a spear phishing attack by sending over private information to the attacker (who’s masquerading as a supplier, client or manager).
Without training on how to recognize a false email address — coupled with policies prohibiting staff from downloading email attachments — your employees could trigger ransomware attacks on your business and, as a result, lock you out of your computers and freeze your operations.
Training is the primary method of dealing with these vulnerabilities. In fact, with training and education, you can improve your cyber security stature relatively quickly and affordably.
Insider Threats in Cyber Security
Where human error could be remedied with training and education, insider threats are a result of malice combined with weaknesses in your IT policies and access controls.
Insider threats often exploit situations where data and applications are accessible to too many company staff members. This is where there aren’t any access controls to restrict certain apps and/or data to only a few vetted employees.
They can also succeed in environments that allow direct logins without multifactor authentication (MFA) or where staff can email or save files to USBs without data loss protection (DLP).
Our cyber security audits will find the system and process gaps
that leave you vulnerable to insider attacks.
Insider threats can flare up in multiple ways, e.g., (1) data theft or espionage and (2) damage via the injection of malicious software into your company’s IT assets.
To combat internal cyber threats, you must invest in access controls and end-user management tools to provision and deprovision data and/or application access. You need to restrict access to sensitive data/applications to only vetted staff who are in need of it for their work. You must also have the ability to rapidly revoke access and, where devices are involved, remote-wipe data.
Insufficient Cyber Security Policy and Procedures
It’s clear that preventing employee errors and mitigating insider threats requires the creation of clear and well-defined cyber security policies and systems.
Your cyber policy should clearly prohibit (and wherever possible, inhibit) your employees from using the company’s IT assets the wrong way. For example, they shouldn’t be downloading or installing attachments from email, browsing on risky websites, falling for phishing attacks from Facebook, Twitter or WhatsApp and other reckless, unnecessary activity.
In terms of systems, mobile device management (MDM) will equip you to restrict access to data and applications on employee devices. You can also block applications downloaded outside of standard channels (e.g., the Google Play store). Finally, in case of lost, stolen and ex-employee devices, you can remote-wipe data and revoke access.
By combining a good cyber security policy with access controls and an audit trail, you will limit the freedom for malicious activity in your company.
At Power Consulting, we understand that SMBs lack the time and resources to clamp down on their cybersecurity threats. That’s why we had spent over 20 years building and honing cyber security consulting, tools and processes centred on the constraints of SMBs. Speak to us today to discuss how we’ll identify and close your cyber security training, policy, system and process gaps with a cyber security assessment to prevent internally-caused breaches and disasters.
Learn More:
- The Complete Guide to Cybersecurity for Small to Medium Sized Businesses
- How to Create a Business Continuity Plan
- Managing Cyber Security Internally VS. Outsourcing to a Provider
- Top 7 SMB Cyber Security Trends in 2019
- How Managed Cyber Security can Protect You Against Cyber Threats
- What’s The Cost of Managed IT Services & How to Manage The Costs
- Is your Managed Service Provider Secure?
- How to Prevent Ransomware Attacks

