
Enterprise IT security threats are becoming more and more prevalent as businesses become more digitized. Hackers are finding new ways to exploit vulnerabilities in enterprise IT security systems every day, so business owners must understand the top threats and take steps to protect their networks and data.
Even more worrisome is that just under half of all cyberattacks target enterprises specifically, and cybercrime continues to be one of the world’s most prolific forms of criminal activity.
But not to worry, because there are several ways to protect the data that is important to you, from digital assets to customer data and everything in between. We can show you how to avoid catastrophic data breaches and the kinds of cyber threats that enterprise businesses should be on the lookout for.
Without further ado, in this blog post, we will discuss the 10 most dangerous enterprise IT security threats and how you can protect your business against them.
But first, a little explainer on the topic itself.
What Is Enterprise IT Security?
Enterprise network security is a set of measures designed to protect the networks, data, users, and applications used by large organizations.
It encompasses a wide range of technologies and processes including authentication systems, anti-malware software, firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), content filtering tools, and more.
The goal of enterprise network security is to practice responsible risk management and defend against malicious intruders or hackers who attempt to gain access to sensitive information such as intellectual property, customer databases, proprietary trade secrets, and other confidential corporate records.
Many enterprise businesses follow the NIST Security Model for managing cybersecurity protection, detection, and response.
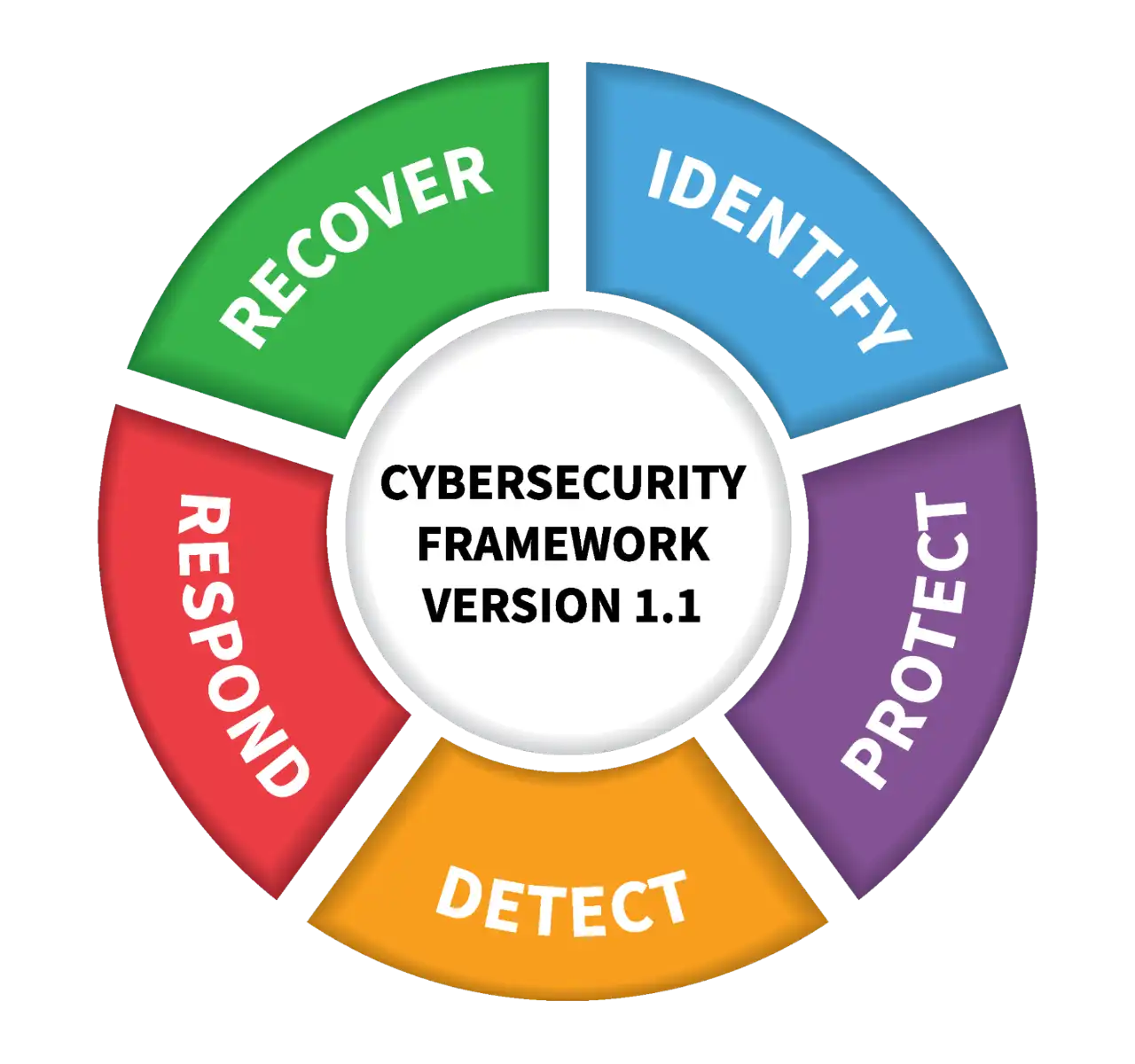
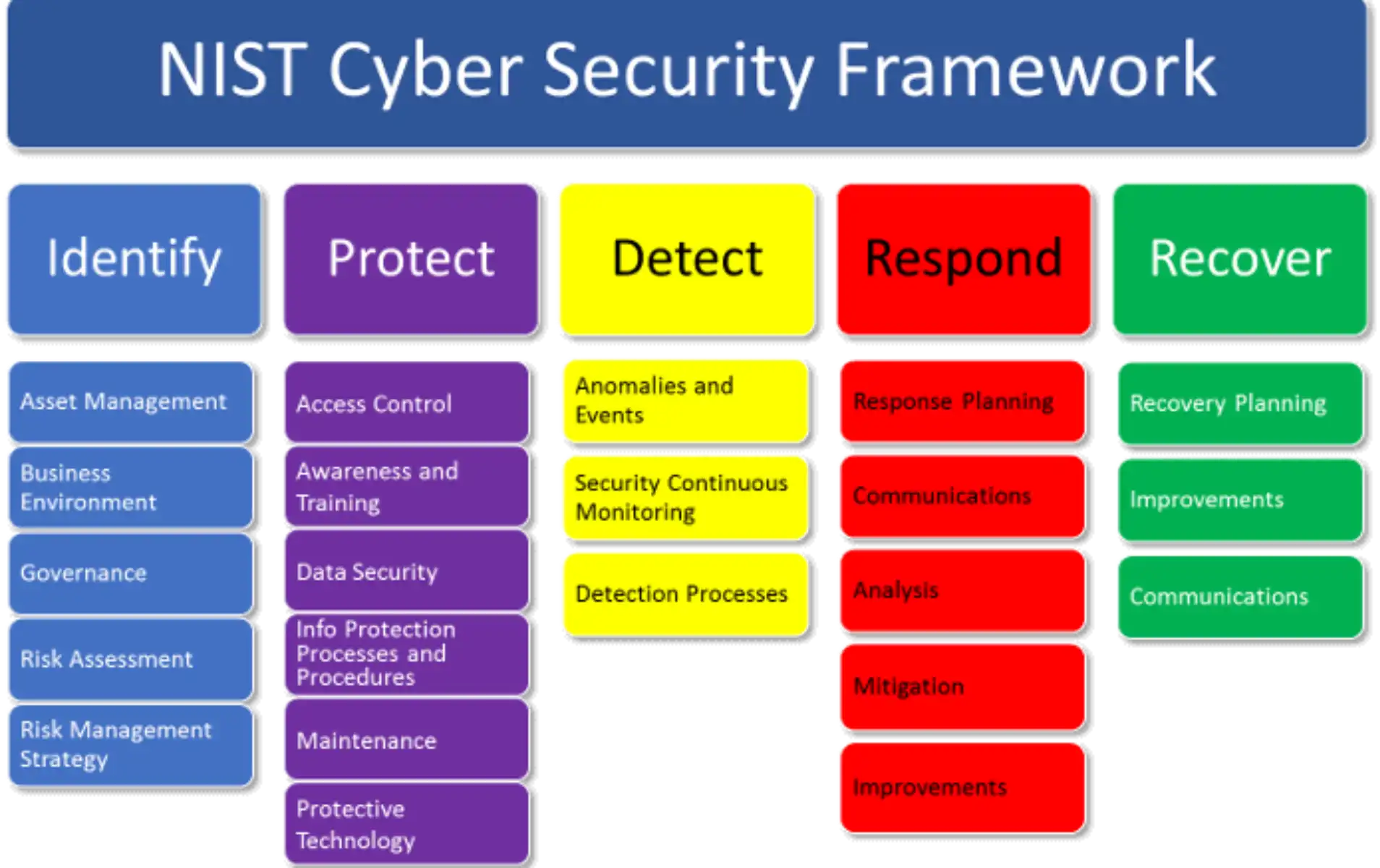
The 5 Biggest Threats to Enterprise IT Security (and How to Protect Against Them)
Despite substantial budgets, multiple security models and the best efforts of trained professionals, enterprise security architecture is by no means invulnerable. There will always be user error, plus constantly a constantly changing threat landscape, and a constantly changing network to protect.
Starting to Feel Like a Managed Cybersecurity Solution Might be the Best Choice for You?
See how we’re the perfect MSP to help with that.
To help you develop your enterprise security strategy, here are 5 of the most dangerous enterprise IT security threats. This way, you’ll be better prepared to protect your digital assets against unauthorized access.
1. Ransomware
Hackers often target smaller businesses because they have fewer security measures. The exception to this statistic is ransomware. 56% of companies with over 100 employees report being ransomware targets, compared to only 37% of companies with less than 100 employees.
Enactors know that most enterprises have more robust cybersecurity measures. Therefore, they may attempt to exploit staff ignorance to get past strong, enterprise-grade software. 90% of successful enterprise ransomware attacks used social engineering tactics to gain system access.
Educate your employees about social engineering and back up all data. Ransomware attacks encrypt stolen data or outright destroy it. Having another version of your data that they haven’t stolen decreases their power in the negotiation.
2. Nation-State Cyber Attacks
A nation-state attack is when cybercriminals enact a cybersecurity breach on a foreign server to further their own country’s agenda. Between 2021 and 2022, the percentage of cyberattacks that fell into this category increased from 20% to 40%, and 79% of these attacks target enterprise corporations.
Like any cybercrime, good cyber hygiene is a great way to prevent nation-state attacks.
However, be aware that nation-state attacks often exploit machine identities, which are the cryptographic codes that allow authentication between devices. To guard against this, use a zero-trust identity management system, conduct regular audits, and rotate encryption keys.
3. Sophisticated Malware Infections
Because hackers know that most enterprises use a more sophisticated security solution, they employ more sophisticated malware to breach their defenses. These malware target vulnerabilities in enterprise-grade firewalls, which makes it hard to keep up.
Consistent network monitoring and frequent patch management will help you stay ahead of sophisticated viruses. A network security audit can help you detect potential weaknesses and proactively patch them. Perform them regularly to keep up with emerging threats.
4. Corporate Account Takeover (CATO)
A CATO attack is when criminals steal employee credentials to impersonate a representative from the company. They may target customers to collect personal information or make fraudulent transactions under the company’s name.
| Become your company’s resident subject matter expert on cybersecurity with these useful blogs: |
Well-known businesses are most vulnerable to CATO attacks due to their familiarity and trust with the public. Attackers need stolen login credentials to do this. They typically get them from phishing, keylogger malware, or hacking an employee’s social media profile or IoT devices.
Implement strict social media policies and use an email filter to block suspicious messages. Choose an antivirus software that can detect keyloggers.
If your company uses legitimate keylogging software, keep an accurate record of what you installed so you can quickly identify irregular tracking
5. Scraping Attacks
Many enterprises use scraping software to create personalized browsing experiences. On the flip side, bad actors scrape data to usurp SEO rankings and imitate legitimate companies to commit fraud. Like CATO attacks, bigger names are more common targets thanks to their recognition.
The simplest way to catch fraudulent imitators is a manual search. From there, you can report the website to have it taken down. You can also prevent scrapers from touching your site with CAPTCHA verifications and by limiting the number of searches per second from each IP address.
Getting Help from Power Consulting with Developing Your Enterprise IT Security Plan
Power Consulting provides enterprise IT security services including:
- Vulnerability assessment
- Cybersecurity strategic plan
- Cybersecurity Managed Services
Our experts will identify your cyber security risks and vulnerabilities, and use that information to create a customized plan to protect your business. We also provide ongoing monitoring solutions to ensure your network remains secure.
Contact us today to start building an effective enterprise IT security plan for your organization!

