
According to a recent survey from the IFEBP, close to three-fourths (74%) of employers now offer hybrid work arrangements for their staffs. While this shift offers flexibility and improved work-life balance, it also introduces critical cybersecurity challenges. Unsecured remote access can expose sensitive company data, leading to financial and reputational risks.
As Chris Power, CEO of Power Consulting, says, “A robust remote access policy is the foundation of secure, productive mobile workforces.”
This guide will walk you through how to create a remote access policy that secures your mobile workforce while ensuring compliance and operational efficiency.
Secure Your Workforce, Protect Your Data—Act Now!
Don’t leave your business vulnerable to cyber threats. Safeguard your remote operations with a robust access policy today.
What is a Remote Access Policy?
Remote access policies are a strategic framework designed to govern how employees, contractors, and third parties can securely access company systems, data, and resources from remote locations. They define the rules, tools, and security measures required to protect the organization’s assets while enabling seamless remote operations.
A policy can typically cover:
- Authentication and Authorization: Ensuring only verified users can access the network.
- Permitted Devices: Outlining the types of devices (e.g., company-issued laptops or BYOD devices) allowed to connect.
- Network Access Levels: Specifying which systems and data are accessible based on roles and responsibilities.
- Usage Guidelines: Establishing acceptable usage practices to minimize security risks.
By addressing these elements, a remote access policy balances security with operational flexibility.
Why Is a Remote Access Policy Important for Mobile Workforces?
As businesses embrace hybrid and remote work models, the number of employees accessing sensitive data from outside the corporate firewall has surged. Without a remote access policy, organizations risk exposing their systems to unauthorized access, data breaches, and non-compliance with industry regulations. Here’s why a remote access policy is essential:
1. Protects Data During Transmission
When employees work remotely, they often rely on public or unsecured networks, such as those in cafes or airports. A robust remote access policy ensures that all data transmitted between devices and company servers is encrypted, reducing the risk of interception by malicious actors.
2. Implements Role-Based Access Controls (RBAC)
Not every employee needs access to all company systems. A remote access policy ensures that access is granted based on the principle of least privilege. For example:
- Executives: May require access to high-level financial data and decision-making tools.
- Customer Service Representatives: May only need access to customer relationship management (CRM) systems.
This segmentation reduces the likelihood of internal data misuse and limits the damage from compromised accounts.
3. Ensures Compliance with Regulatory Standards
Industries like healthcare, finance, and education are subject to strict data privacy and security regulations, such as HIPAA, PCI DSS, or GDPR. A well-defined remote access policy helps organizations comply with these standards by:
- Establishing secure access protocols.
- Enforcing data encryption.
- Monitoring and auditing remote access activity.
4. Minimizes Cybersecurity Threats
Remote work opens up new attack vectors, such as phishing attempts, man-in-the-middle attacks, and malware infections. By mandating measures like multi-factor authentication (MFA) and endpoint protection, a remote access policy can significantly reduce the risk of cyber threats.
5. Boosts Employee Productivity
Contrary to misconceptions, a remote access policy isn’t just about security—it’s also about ensuring that employees can work efficiently and without interruption. By providing clear guidelines and secure, reliable access to necessary resources, employees can focus on their tasks without worrying about connectivity or security hurdles.
6. Facilitates Rapid Scaling and Flexibility
A remote access policy provides a scalable framework that adapts to organizational growth and evolving workforce needs. Whether onboarding new employees, integrating contractors, or enabling work-from-anywhere scenarios, the policy ensures consistent security and operational efficiency.
A well-crafted remote access policy isn’t just a document—it’s a cornerstone of modern business operations. By clearly defining how remote access is managed, organizations can protect their resources, meet compliance requirements, and empower their workforce to thrive in a mobile-first world.
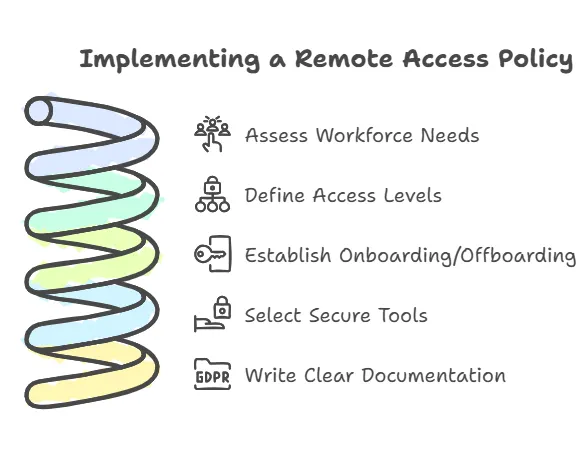
How to Develop Custom Remote Access Policies
Creating a custom remote access policy tailored to your organization’s unique needs is critical for ensuring security, compliance, and productivity. Here’s a step-by-step guide to building a comprehensive and effective policy:
1. Assess Your Workforce’s Needs
Before drafting the policy, you must understand your workforce’s specific remote access requirements. This involves:
- Identifying Roles and Responsibilities:
Map out which roles need access to specific systems, applications, and data. For example, IT administrators may require access to backend systems, while sales teams may only need access to CRM software. - Analyzing Work Habits:
Evaluate how your employees work remotely. Are they using personal devices, or are they provided with company-issued hardware? Do they often work from public spaces? These insights will help address potential security gaps. - Considering External Users:
Account for third parties like contractors, vendors, or partners who may need temporary or limited access to your systems.
A thorough needs assessment ensures the policy is aligned with your team’s workflows and minimizes unnecessary restrictions that could hamper productivity.
2. Define Access Levels
Clearly outlining access levels is crucial for preventing unauthorized access and safeguarding sensitive information. This is achieved through:
- Role-Based Access Control (RBAC):
Implement the principle of least privilege, granting users access only to the data and systems they need for their roles. Examples include:- HR staff accessing employee records but not financial data.
- Marketing teams accessing analytics platforms but not server configurations.
- Contextual Access Permissions:
Define conditions under which access is granted. For instance, you might restrict certain systems to office networks or allow temporary access for specific projects. - Restricting Administrative Privileges:
Limit administrative rights to essential personnel, reducing the risk of accidental or malicious changes to critical systems.
By defining granular access levels, you can minimize security risks while ensuring employees have the resources they need to perform effectively.
3. Establish Protocols for Onboarding and Offboarding
Managing access credentials effectively is a key part of any remote access policy. A well-defined onboarding and offboarding process includes:
- Swift Onboarding Procedures:
- Provide employees with secure login credentials and access to the tools they need from day one.
- Verify devices before granting access to ensure they meet security standards.
- Effective Offboarding Practices:
- Immediately revoke access to all systems when an employee leaves the organization.
- Recover company-issued devices or remotely wipe data from personal devices, if allowed by policy.
- Periodic Access Reviews:
Conduct regular audits to identify dormant accounts or outdated access permissions. This prevents ex-employees or unused accounts from becoming potential entry points for cybercriminals.
4. Select Secure Tools and Technologies
The right tools and technologies form the backbone of a secure remote access policy. Consider the following:
- Virtual Private Networks (VPNs):
Encrypt internet connections, providing a secure channel for remote employees to access company resources. - Endpoint Protection:
Deploy antivirus software, firewalls, and intrusion detection systems to safeguard employee devices. - Multi-Factor Authentication (MFA):
Add an extra layer of security by requiring two or more forms of verification before granting access. - Zero Trust Architecture:
Shift from traditional perimeter-based security to a model that continuously verifies user identities and device integrity, even after access is granted. - Secure Collaboration Tools:
Use encrypted platforms for file sharing, messaging, and video conferencing to prevent data leakage.
Selecting tools that align with your organization’s size, budget, and compliance needs ensures a strong security foundation.
5. Write Clear and Accessible Documentation
A policy is only as effective as its implementation, and clear documentation is key to ensuring adoption. To make the policy user-friendly:
- Avoid Jargon:
Use plain language to explain the rules, tools, and procedures. For example, instead of saying, “Utilize a robust encryption mechanism,” say, “Use tools that encrypt data to protect sensitive information.” - Provide Visual Aids:
Include diagrams or flowcharts to illustrate processes like logging into the VPN or requesting access to restricted systems. - Outline Consequences:
Specify the repercussions for non-compliance, such as disciplinary action or restricted access. - Create a Quick Reference Guide:
Provide employees with a condensed version of the policy for easy day-to-day use.
Effective documentation bridges the gap between policy design and real-world application, ensuring that all users understand and comply with the rules.
Enforcing Your Remote Access Policy: Examples and Best Practices
Implementing a remote access policy is just the beginning. Effective enforcement ensures its success:
1. Use Monitoring Tools
Leverage technology to track access activity and detect anomalies:
- Access Logs: Record who accessed which systems and when.
- Behavioral Analytics: Identify unusual patterns, such as logins from unexpected locations.
- Real-Time Alerts: Get notified of failed login attempts or unauthorized access.
2. Conduct Regular Policy Reviews
Update the policy regularly to address:
- Evolving cybersecurity threats.
- Changes in business operations or workforce needs.
- Feedback from employees about policy usability.
3. Ensure Regulatory Compliance
Maintain alignment with laws and standards like GDPR and HIPAA by incorporating:
- Strong encryption protocols.
- Detailed audit trails for access logs.
- Regular compliance checks.
4. Provide Role-Based Access Examples
Clear examples help enforce RBAC effectively:
- Employee A: Limited to HR systems for payroll management.
- Employee B: Full administrative rights to IT tools for troubleshooting.
- Contractor C: Temporary access to specific project management tools.
Common Pitfalls to Avoid
Avoid these mistakes when implementing your remote access policy:
1. Overcomplicating the Policy
Complex policies discourage compliance. Use concise language and provide summaries for ease of use.
2. Neglecting Employee Training
According to CloudSecureTech, 56% of employees lack the knowledge to respond effectively if a breach occurs. Untrained employees are vulnerable to cyber threats. Conduct regular training on secure practices and policy updates.
3. Failing to Test the Policy
Simulate real-world scenarios to identify weaknesses. Regular testing ensures the policy works effectively under all conditions.
Table: Step-by-Step Guide to Creating a Remote Access Control Policy
| Step | Action |
| Assess Needs | Identify workforce access requirements. |
| Define Access Levels | Assign permissions based on roles. |
| Select Security Tools | Implement VPNs, MFA, and firewalls. |
| Draft Documentation | Write a clear, accessible policy. |
| Train Employees | Educate staff on policy and tools. |
| Monitor and Review | Regularly audit and update the policy. |
| More articles you might like: |
Secure Your Mobile Workforce with Power Consulting’s Expertise
A well-designed remote access policy is more than just a document—it’s your first line of defence in protecting sensitive data while empowering your workforce to stay productive from anywhere. By assessing your needs, defining access levels, and enforcing robust security measures, you can safeguard your business against evolving cyber threats.
Power Consulting specializes in delivering tailored network security solutions that ensure your organization stays secure and compliant. With our expertise, you can confidently manage remote access and protect your valuable assets.
Don’t leave your mobile workforce unprotected. Contact Power Consulting today to schedule a personalized consultation and take the first step towards a more secure future.
| Find Powerful Cybersecurity Security Services in NYC | ||
| Manhattan | ||




