
Imagine this: You’re casually browsing the web, managing your online accounts, when suddenly, a hacker gains unauthorized access to your session. This isn’t a sci-fi scenario—it’s a real threat. In fact, a 2024 report by Imperva reveals that session hijacking is among the top methods used in web application attacks, exploiting vulnerabilities such as cross-site scripting (XSS) and man-in-the-middle (MITM) techniques.
As Chris Power, CEO of Power Consulting, says, “Session hijacking is not just a technical issue; it’s a critical threat to your personal and business data in today’s connected world.”
Understanding what is session hijacking and how to prevent session hijacking is crucial for safeguarding your digital assets.
What Is Session Hijacking?
Session hijacking occurs when an attacker takes control of a user’s active session with a web application. Essentially, the hacker impersonates the user to access sensitive information, including personal data and financial records.
Is Your Data Secure Enough?
Discover how Power Consulting can safeguard your sessions and protect against hijacking attacks
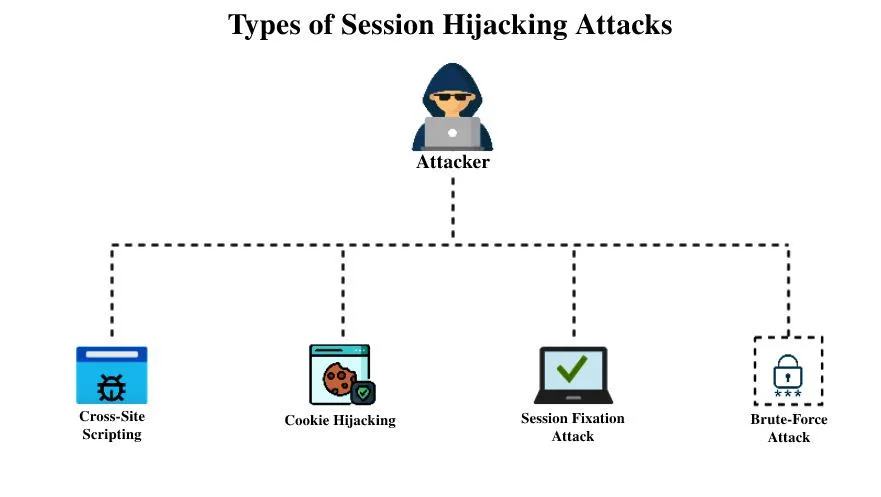
Types of Session Hijacking
- Active Hijacking: The attacker takes over the session in real-time and interacts with the user’s application.
- Passive Hijacking: The attacker silently observes the session to gather information without disrupting the user’s activities.
Common Techniques Used in Session Hijacking
- Session Fixation: The attacker forces the user to use a specific session ID, which the attacker later exploits.
- Session Sidejacking: This method involves intercepting unencrypted session data over a network, often using packet-sniffing tools.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into a website, executing in the user’s browser and stealing session data.
Source: GeeksforGeeks
How Does Session Hijacking Work?
Understanding session hijacking in cybersecurity is key to protecting yourself and your business.
Step-by-Step Process
- User Initiates a Session: You start a session with a web application by logging in.
- Attacker Intercepts the Session ID: The attacker uses various techniques to steal or intercept your session ID.
- Attacker Gains Unauthorized Access: With the session ID in hand, the attacker can now impersonate you, accessing your account and sensitive data.
Real-World Example
Imagine logging into your bank account over public Wi-Fi. Without your knowledge, a hacker could use session sidejacking to intercept your session ID and gain access to your account, enabling unauthorized transactions and compromising your financial security.
| More articles you might like: |
The Impact of Session Hijacking
The consequences of session hijacking can be severe, affecting both individuals and businesses.
For Individuals
- Identity Theft: Hackers can use your session to impersonate you, leading to identity theft and unauthorized use of your personal information.
- Unauthorized Transactions: Cybercriminals can access your financial accounts, making unauthorized transactions and stealing your money.
For Businesses
- Data Breach: Session hijacking can lead to massive data breaches, exposing sensitive customer and company information. In 2024, the average cost of a data breach is around $4.88 million, according to IBM’s Cost of a Data Breach Report.
- Financial Loss: Companies may face significant financial loss due to fraudulent transactions and the cost of mitigating the breach.
- Reputation Damage: A data breach resulting from session hijacking can irreparably harm your business’s reputation.
Session Token Hijacking & Business Email Compromise
While brute-force attacks have been common, another growing threat is token hijacking, which allows hackers to bypass multi-factor authentication (MFA) and conditional access.
How Token Hijacking Works:
- A hacker sets up a server between the user’s login screen and the SaaS service (like Microsoft 365).
- The hacker sends an email, often impersonating someone the user knows, with a link to the SaaS application.
- The user clicks the link, thinking it’s legitimate.
- They enter their credentials, creating an access token sent to the browser.
- The hacker intercepts this token to access the user’s account.
How to Spot Token Hijacking
Look for unusual account activity, such as:
- Login attempts from unfamiliar locations.
- Changes in account settings, like email forwarding or MFA modifications. These indicators can signal a compromise.
How to Protect Against Session Hijacking
Proactively taking steps to prevent session hijacking is crucial for protecting your digital assets.
- Use Secure Connections (HTTPS): Always ensure your connection to websites is secured with HTTPS to encrypt data transmission, making it difficult for attackers to intercept your session ID.
- Implement Strong Session Management:
- Token Binding: This method ensures that session tokens can only be used by the originating server, preventing them from being exploited by attackers.
- Conditional Access: Implement conditional access policies to require users to meet specific criteria (e.g., location, device compliance) before accessing applications, enhancing overall security.
- Phishing-Resistant MFA Tokens: Use multifactor authentication (MFA) that employs hardware tokens or biometric data, which are more resilient to phishing attempts.
- Employ Secure Cookies: Set your session cookies with the HttpOnly and Secure flags to protect against unauthorized access.
- Employ Anti-XSS Techniques: Validate and sanitize input to protect against XSS attacks that could lead to session hijacking.
- Regular Software Updates: Keep your software, web applications, browsers, and plugins updated to reduce vulnerabilities.
- Monitor and Log Sessions: Implement real-time monitoring to detect suspicious activity, such as multiple logins from different locations.
Best Practices to Prevent Session Hijacking
| Best Practices for Users | Description |
| Avoid Public Wi-Fi | Public Wi-Fi networks are a hotbed for hackers looking to steal session IDs. If you must use public Wi-Fi, consider using a Virtual Private Network (VPN) to encrypt your connection. |
| Use VPNs | VPNs provide an additional layer of security by encrypting your internet connection, making it much harder for attackers to intercept your data. |
| Be Cautious with Links | Avoid clicking on suspicious links, especially in unsolicited emails or messages, as these can lead to phishing sites designed to steal your session data. |
| Enable Two-Factor Authentication | Add an extra layer of security by requiring a second form of verification in addition to your password, such as a code sent to your phone. |
| Log Out When Finished | Always log out of websites and applications when you are done, especially on shared or public devices, to prevent unauthorized access to your sessions. |
| Keep Your Devices Secure | Use strong, unique passwords and keep your devices updated with the latest security patches and antivirus software to reduce vulnerabilities. |
| Regularly Clear Browser Cookies | Clear your browser cookies regularly to remove session data that could potentially be exploited by attackers. |
Safeguard Your Business from Hijacks & Cyberthreats With Power Consulting
According to research by CloudSecureTech, on an average, a data breach can cost a business millions, and sadly, 60% of small businesses have to close down within six months after a cyber attack.
Session hijacking is a serious cybersecurity threat that can have devastating consequences. By understanding what is session hijacking and implementing the right session hijacking prevention strategies, you can significantly reduce your risk of falling victim to this type of attack.
| Discover Trusted Cybersecurity Services in New York |
Power Consulting is a leading provider of comprehensive cybersecurity solutions designed to help you safeguard your digital assets. Contact Power Consulting today to learn more about how we can properly protect your business, users and intellectual data.



