
Over 80% of American businesses report their IT environment being breached successfully. And in case you were wondering, “I’m too small to be attacked” or “We’re too large to be breached”, think again.
Everyone’s fair game for cybercriminals–85% of companies with fewer than 1,000 employees and more than 60% of large businesses have been successfully invaded. But what exactly is a security breach?
“Understanding the nature of threats is paramount. It’s not just about defending against attacks; it’s about fostering a culture of proactive vigilance and resilience. This is the bedrock upon which secure businesses are built.”
– Chris Power, CEO of Power Consulting
Definition of a Security Breach
A security breach occurs when someone gets into your computer systems, networks, or devices without authorization, leading to your information being accessed illegally. Effectively, a cybercriminal or malware can bypass your cybersecurity measures and infiltrate your IT systems.
It’s like someone breaking into your house, but in this case, they’re breaking into your IT systems.
There’s a key difference between a security breach and a data breach. Think of a security breach as the moment a thief enters your house and a data breach as the moment they steal something valuable, like your wallet or laptop.
Confidential information is extremely valuable and can be sold on the dark web, where customer information and credit card numbers might be used for identity theft or fraud. Alternatively, accounts and data may be held at ransom, forcing a business to pay to release it.
Security breaches are expensive, costing large companies over $4.45 million. For SMBs, it’s even more alarming–60% of small and mid-sized businesses never recover from a breach.
It’s also crucial to understand that not all security problems are considered breaches. For example, getting a virus, being hit by a DDoS attack, or an employee losing a laptop doesn’t necessarily mean there was a security breach unless these actions lead to unauthorized access or data loss.
6 Common Security Breaches (and How They Happen)
There are various ways a security breach can happen, depending on the method used to gain unauthorized access to a system.
Malware: This is harmful software, like viruses, worms, ransomware, and spyware, designed to damage a system or sneak into it without permission.
Social engineering: This method involves tricking people into giving away their personal or sensitive information. It’s done by pretending to be someone or something the victim trusts. Phishing attacks are a popular strategy, where attackers might use fake identities to seem more credible.
| Small businesses also face way more trickery attacks like phishing than big companies—about 350% more. |
Physical security breaches: These happen when someone gets into a building or physical device without authorization. Sometimes, tricks like vishing (voice phishing) are used to get someone inside to give away access.
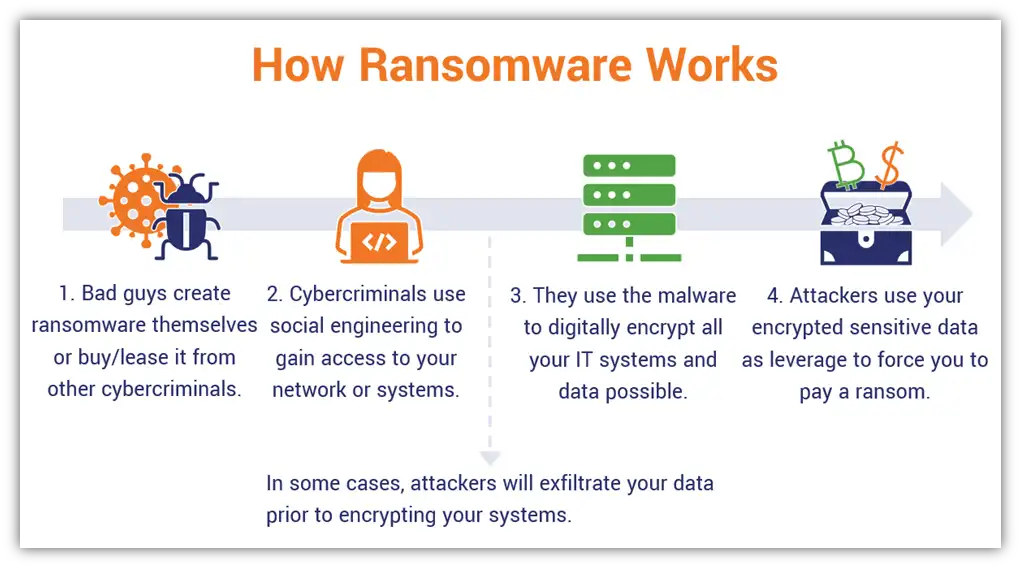
Ransomware attacks: A type of malware that locks you out of your files by encrypting them. Victims must pay a ransom to get the keys to unlock their files and access them again.
DDoS attack: This attack overloads a website (or other web properties) with so much traffic that it crashes. It’s a hacking technique that can break down the server’s security defenses by overwhelming them.
Man-in-the-middle attack: In this attack, a hacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating. This allows attackers to intercept and misuse sensitive data.
What Should You Do in the Event of a Security Breach?
If you discover that your own systems have been compromised or those at a company you do business with have experienced a security breach, time is of the essence. Here’s a broad list of items to address. Mind you, depending on your IT and operations, there will be other remedial actions to consider.
- If you’re caught in a breach involving your financial information, quickly alert your banks and any financial institutions you use. Change all your passwords, security questions and PINs, if applicable.
- Try to determine what information was stolen to understand how serious the breach is. If someone got hold of your customer lists or confidential information, you need to act quickly.
- After a breach, be wary of giving out information, even if it seems like the request is coming from a recognizable source. It could be a trick. Instead, verify the request through official channels.
- Stay alert for tricks like social engineering attacks. For example, a criminal could pretend to be calling from a known vendor you work with, asking you to ‘update the account you normally wire money to.’
- Keep an eye on your accounts for any unusual activity and address unrecognized interactions immediately.
- Depending on the state you’re located in, you may be obligated to alert all users impacted by the breach expeditiously. Again, work with your cybersecurity team to identify what (if anything) was stolen and what its impact might be.
| 💡 Keep in mind, if one of your accounts has suffered a security breach, it means your other accounts might be in danger too, especially if you use the same passwords or frequently conduct transactions between them. |
Tips for Protecting Yourself Against Breach of Security
No business can be completely immune to a security breach. That said, there are many steps you can take to mitigate the risk and magnitude of breaches.
- Foster a culture of strong passwords in your organizations by mixing upper and lower-case letters, numbers, and symbols, making them tough to crack. Also, enforce multifactor authentication for all users.
- Implement policies to have unique passwords for each user and account to prevent a hacker who accesses one account from breaking into all of them. This way, if one account is compromised, the damage is limited.
- Close accounts you no longer use to reduce your risk of a security breach. Unused accounts can go unnoticed if compromised, potentially giving hackers access to your active accounts.
- Follow industry best practices when disposing of old data storage devices. Devices should be thoroughly wiped using data destruction software and physically destroyed.
From 24/7 Monitoring to Audit-Readiness Assessments
Leverage the expertise of a team that has secured businesses like yours for over 30 years
- Implement effective data backup organization-wide. In case of a ransomware attack where files are encrypted, having backups on a separate drive ensures your information remains accessible. Backups will also protect you in the event data is deleted accidentally.
- Have a clear Mobile Device Management policy and system, allowing you to secure mobile devices. Pay particular attention when you’re onboarding and offboarding employees.
- Ensure your team receives security awareness training routinely. It will instill password hygiene, email vigilance, and preparedness for social engineering. Cybersecurity experts can also make training more relatable by providing practical insights your team can identify with.
- Employ encryption for data at rest and in transit to minimize damage. Even if an attacker can steal your data, they cannot access or use it.
| More articles you might like: |
Protect Your Business Against Security Breaches
Though cybersecurity can never be perfect, that doesn’t mean you don’t do everything in your power to keep your business safe. Navigating the complexities of cybersecurity can be daunting for businesses.
This is where Power Consulting excels. With our comprehensive approach to cybersecurity strategy, management, and support, we provide the expertise and services necessary to protect your digital assets effectively. Our multi-layer cybersecurity protections are based on the NIST model. To align your company’s cyber protections with industry best practices – affordably – call Power Consulting.
| Trusted Cybersecurity Services Near You
|
Talk to us to determine how we secure businesses like yours and help you lower risk ratings.



