
Regular cloud security risk assessments are necessary because they identify vulnerabilities and allow you to adjust your security measures accordingly. As your cloud environment grows, new risks may emerge. Frequent assessments help you detect these risks early so you can swiftly mitigate them.
“Like any form of risk management, cloud security is never a one-and-done process. You need a proactive strategy to stay ahead of evolving security issues.” – Chris Power, CEO of Power Consulting.
In some cases, regular cloud risk assessments are a compliance requirement. For example, the International Organization for Standardization (ISO) includes regular risk assessments in its standards. ISO/IEC 27001:2013 specifies that organizations must “conduct risk assessments at planned intervals” on all data storage technologies, including cloud computing.
Whether it’s required for compliance or not, you need to know how to perform a cloud security assessment correctly. This article is here to help you in that effort. We will explore how often you should perform cloud assessments, what to include on your checklist, and what tools can help you simplify the process.
How Often Should You Perform a Cloud Security Assessment?
You must perform a cloud security assessment at least annually. However, we highly recommend performing your assessments every quarter. You may also periodically need to perform one off your regular schedule. Significant changes, such as new applications, configurations, or updates, should also prompt cloud re-assessments.
It’s also important to perform one after a security incident occurs. A post-incident assessment will help you pinpoint how the incident happened so you can prevent similar issues in the future.
Get a Full Suite of Cloud Services That Keeps You Compliant With
GDPR
SSAE 16
HIPPA
PCI
What to Include on Your Cloud Risk Assessment Checklist
The following is what you need to add to your cloud security assessment checklist. Each item includes multiple factors, so we have also included a quick grid beneath each item to help you keep track of everything you need to know.
✔ Data Protection
Protecting sensitive data is a top priority in cloud environments. Ensure data is properly classified, encrypted both in transit and at rest, and protected by the correct access controls.
| Data classification | Assess the sensitivity of data stored in the cloud. |
| Data encryption | Verify encryption protocols for data in transit and at rest. |
| Data access controls | Confirm the use of role-based access controls and least-privilege principles. |
| Data residency & sovereignty requirements | Confirm that data storage locations meet your country’s or region’s legal requirements. |
✔ Identity and Access Management (IAM)
Effective IAM practices prevent unauthorized access to cloud resources. 80% of data breaches are caused by attackers stealing passwords, and implementing IAM security controls reduces that risk.
| Multi-factor authentication (MFA) | Implement MFA for accessing your cloud service. |
| Identity governance | Monitor and manage all user access privileges. |
| Privileged access management (PAM) | Manage and monitor access from accounts with elevated permissions to protect critical cloud resources. |
✔ Network Security
A secure network architecture is essential for defending against external threats. Strong network security practices also create multiple layers of defense. Therefore, if one layer is breached, the attacker will have another layer in their way.
| Virtual network configuration | Verify correct network segmentation and access control lists (ACLs). |
| Intrusion detection and prevention | Ensure that IDS/IPS tools are in place. |
| Firewall settings | Configure cloud-based firewalls for controlled access. |
| VPN & secure access points | Ensure secure connections between on-premises and cloud environments. |
✔ Application Security
Cloud applications need protection against vulnerabilities that could be exploited. Addressing security risks within cloud-based software helps ensure applications remain both secure and functional.
| Application-layer security | Assess security in applications hosted on the cloud. |
| Vulnerability management | Regularly scan for and remediate vulnerabilities. |
| Secure DevOps (DevSecOps) | Integrate security practices within the development lifecycle (if applicable to your operations). |
✔ Endpoint Security
Since cloud resources are accessed from various devices, endpoint security is critical. One compromised endpoint could lead to rapid network spread if not carefully managed.
| Device management | Ensure secure access to the cloud from various devices. |
| Endpoint protection | Confirm endpoint security measures like antivirus and anti-malware on each connected device. |
✔ Incident Response
Having a rapid response capability limits the impact of security incidents. A clear incident response and recovery plan helps quickly contain issues, so you can reduce data loss and maintain operational continuity.
| Incident response plan | Develop and test a cloud-specific incident response plan. |
| Data backup | Check backup frequency and recovery point objectives (RPO). |
| Disaster recovery | Assess your cloud provider’s disaster recovery system. |
✔ Monitoring & Logging
Continuous monitoring and logging of activities in the cloud offer visibility into potential threats and unusual behavior. Centralized logging and automated alerts enable quick detection and response, which reduces the likelihood of escalated issues.
| Activity logging | Enable logging for user actions, data access, and configuration changes. |
| Security monitoring | Set up alerts for unusual or suspicious activity. |
| Integration with SIEM | If possible, centralize and analyze logs using an SIEM platform. |
✔ Third-Party Risk Evaluation
As cloud services often involve third-party providers, managing risks tied to vendors is crucial. Regular security evaluations of third-party practices help control data access and address any risks related to external providers.
| Vendor assessment | Review the security posture of third-party partners. |
| Data sharing policies | Understand how and with whom your partners share your data. |
| Exit strategy | Plan for the possibility of transitioning away from a partner if their security measures are inadequate. |
Cloud Assessment Tools That Make The Whole Process Easier
Today, 60% of companies are investing in technology tools specifically for risk and compliance management. However, not all of these tools will help you with cloud risk assessments – but here is a list of some of the ones that will.
Cloud Security Posture Management (CSPM)
CSPM tools identify misconfigurations and compliance gaps in cloud environments. These tools accomplish this task by continuously monitoring settings across cloud assets to scan for issues that could introduce vulnerabilities.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM tools oversee identity and permission management within cloud platforms. These tools control access rights to minimize the risks of excessive or unused permissions.
| Learn More About Enhancing Your Cloud Deployments |
Cloud Threat Intelligence Platforms
These platforms collect and analyze threat data specific to cloud infrastructures. Having access to this data can help your cloud management team stay ahead of potential risks and make timely adjustments to security strategies.
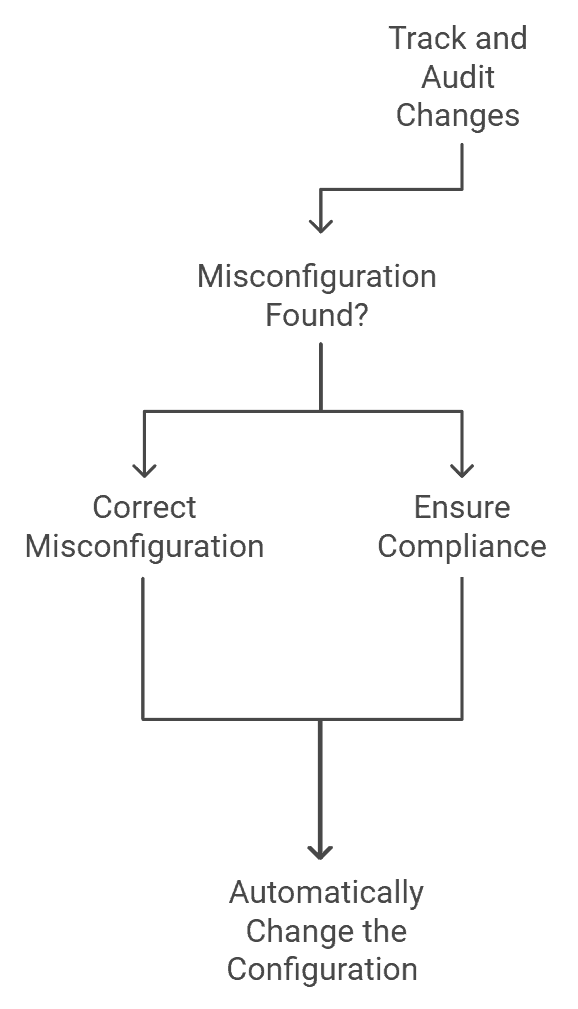
Configuration Management Tools
These tools track and audit configuration changes to reduce the likelihood of insecure configurations. They can also automate cloud configuration processes to ensure all settings align with your security and organizational requirements.
Here is a quick overview of that process.
Cloud Workload Protection Platforms (CWPP)
CWPPs provide vulnerability assessments and runtime protection to address workload-specific threats. This includes both current and emerging issues that may affect your cloud-hosted applications.
| Find Experts in NYC Who Can Lead Your Assessment Process | ||
| Manhattan | Brooklyn | Queens |
Simplify Your Next Cloud Security Assessment With Expert Help
Using the right tools and the right strategy will make your cloud security assessment simpler and more accurate, but bringing in cloud experts can make it even better. If you’re searching for those experts, you can find them from Power Consulting. Our 24/7 team knows how to reduce your IT issues by 45% within your first 3 months of working with us.
Contact us today to get started.



