According to a Ponemon Institute study published in 2017 (via CSR), there was a 50% increase in small and medium-sized businesses (SMB) reporting data breaches compared to 2016. In its 2018 Cyber Security Report, Cisco states that 53% of SMBs had dealt with a data breach.
Cyber security vulnerabilities are clearly a concern for SMBs, but addressing the issue isn’t straightforward, as there are many elements and moving parts in play. For example:
- The technology or systems you have in place (e.g., firewalls, anti-virus software, etc)
- the procedures governing their use
- The training and security credentials of the people using these systems and procedures
- The procedures governing how you respond to a data breach, manage staff access to data and applications, and compliance with regulatory requirements.
- Your staff and the level of cyber security training and support you provide them.
- Cyber security requirements stemming from industry-specific compliance issues.
Each of these security areas presents a distinct management challenge. Few companies have dedicated staff or expertise to prevent or respond to data breaches.
Your organization may have cyber security vulnerabilities which hackers can exploit. In this article, we focus on the leading cyber security gaps of SMBs.
1. Risk Management and Governance
Your cyber security investment is influenced by what you consider as ‘risk’ — i.e., an area which is both vulnerable and in need of protection.
Let’s say you’re a small financial firm in New York: you must comply with regulations set by the Financial Industry Regulatory Authority (FINRA), Securities and Exchange Commission (SEC) and regional bodies such as the New York Department of Financial Services (NYDFS).
You could also be accountable for overseas regulations. For example, if you have clients in the European Union (EU), you will need to follow the General Data Protection Regulation (GDPR).
The GDPR and NYDFS both require you to view data breaches as extremely high-risk. Both also impose rigid rules on how data may be managed at your company and, in case of a data breach, to report the breach within a specified period of time.
If you fail to comply, you could be liable to hefty fines. To avoid these issues, you must put data security top-of-mind and invest in the systems necessary to meet those goals, such as real-time threat sensors and enterprise-grade data centers.
However, if you’ve incorrectly understood your risks and priorities, then you may not have the right IT security measures in place. As a result, you will be vulnerable to your actual cyber threats nor the correct response mechanisms in case of cyber attack incidents or breaches.
Learn More:
2. IT Asset Management
Desktops, laptops, mobile devices, routers, software applications or severs: SMBs have their share of IT assets. If left unprotected, hackers will use your assets to attack your company.
These IT asset management gaps can occur in a variety of ways, such as:
- Your computers might lack active anti-virus software. This puts your computers at risk of getting infected by malware, such as ransomware and spyware.
- You’re not using mobile device management (MDM) to implement organizational policies on employee smartphones. Without MDM, you won’t be able to remote-wipe your data or applications from lost and stolen devices.
- Your business doesn’t have strong access control policies to restrict employee access to non-public information. In other words, too many people at your company can view your private or confidential information.
- You’re not decommissioning your devices properly and, as a result, company data is still on old hardware that you might throw away, sell or donate to others.
3. Vulnerability Assessments (and Penetration Tests)
It isn’t enough to just install anti-virus software and use firewalls. You also need vulnerability scans to find gaps, such as inactive anti-virus software and open ports, in your IT system.
Without these scans, you’re not getting an accurate picture of your cyber security posture and, as a result, could be at risk of a cyber breach.
Penetration tests help gauge the effectiveness of your cyber security system against current and emerging threats. Short of a real-world cyber attack, a penetration test is the only way to assess the effectiveness of your cyber security efforts as well as find and close potential gaps.
Learn More:
Is Your Company At Risk of a Cyber Security Attack?
4. Patch Management
The cyber threat landscape is always evolving. There are new types of malware emerging on a daily basis and your anti-virus software would be of little use if it’s unable to identify new threats.
However, many businesses neglect to update their anti-virus software with the threat definitions released by software vendors. Likewise, it’s easy to ignore or neglect updates and bug-fixes for your productivity applications and other software.
5. Social Engineering & User Training
According to the Ponemon Institute’s study (via CSR), SMBs reported that the leading attacks against them were from phishing and other social engineering methods. Likewise, Cisco found that “well-crafted phishing” attacks were among the top cyber threats posed to SMBs.
Most Frequent Cyber Attack Types Against SMBs
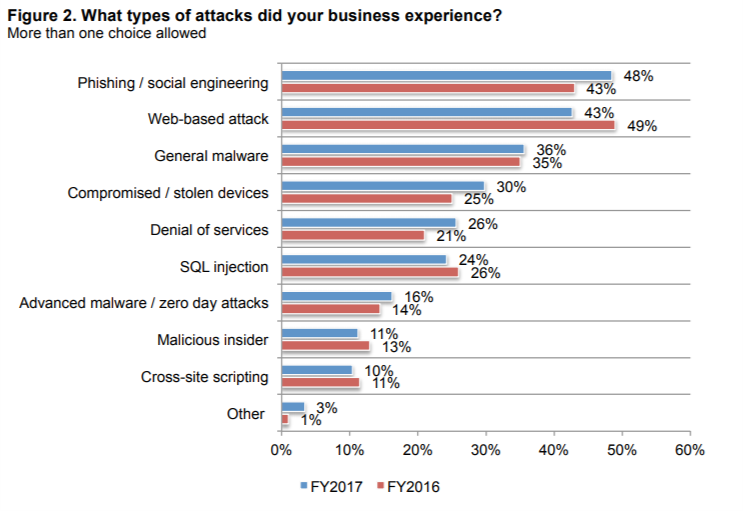 Source: Ponemon Institute via CSR
Source: Ponemon Institute via CSR
While firewalls and anti-virus software can mitigate the risk, cyber attackers aim their phishing attacks at end-users, i.e., your employees.
The lack of clearly-defined cyber-use policies governing how employees may use corporate IT assets and inadequate cyber security training is the leading weaknesses to phishing attacks.
Learn More:
6. Business Continuity Planning
Many businesses make the mistake of not planning for the worst-case scenario — a breach or fatal error. A good backup will allow your data to be fully restored, but without a business continuity plan, you will not be able to quickly restore your business operations back to normal.
Learn More:
7. Multi-Factor Authentication
Some SMBs assume that setting strong passwords is enough. Yes, strong passwords are a must, but if they leak or are cracked, then your IT system is open for the hacker.
In such cases, business has failed to invest in redundancies such as multi-factor authentication (MFA). With MFA, your employees can block outside and/or unrecognized logins.
8. Third Party Vendor Management
SMBs rely on numerous external vendors for IT, such as cloud service providers, software as a service (SaaS) vendors and others. However, many SMBs also lack policies to govern their third-party relationships and, as a result, are at risk of cyber security gaps and compliance problems.
For example, healthcare providers must ensure that their cloud hosts follow HIPAA. If not, the healthcare organization could be fined by the government as well as be at risk of a data breach due to inadequate safeguards by the vendor.
9. User Provisioning and Management
The lack of access controls is also common. In this case, too many employees in the company have access to sensitive data, leaving the business exposed to insider theft or attacks.
Moreover, there are no systems to restrict access or to revoke it from lost and stolen devices as well as ex-employee accounts.
10. Incident Response Planning/Procedures
There are moments where your cyber security systems may fail. For example, a breach can occur because an employee falls for a phishing attack and triggers a ransomware attack.
Unfortunately, many SMBs lack clearly defined procedures for responding to such incidents. For example in a ransomware attack, the correct response is to restore (via disaster recovery), not to pay the ransom or engage the hacker in any way.
Moreover, regulators require you to report a breach within a specific time period, e.g., 72 hours in the case of the New York Department of Financial Services (NYDFS). Failing to notify users and regulators of a breach on time will result in penalties and legal trouble.
Closing the Gaps
Be it due to limited funding or qualified human resources or technical complexities, most SMBs have cyber security vulnerabilities. These gaps are generally found in hardware, software, standard operating procedures, access control privileges, and training.
It’s critical that business owners and operators understand the best available solutions to these issues before determining priorities and taking next steps. Before investing any further, contact Power Consulting to get clarity of how cyber security consulting can stop attackers from exploiting your IT systems.
Learn More:

